Whitehat claims a bug fix inadvertently led to the $200M Euler attack
A pseudonymous whitehat known as Kankodu claimed they submitted a bug bounty report that introduced a specific vulnerability on Euler Finance, subsequently resulting in $200 million attack on the decentralized lending protocol in March.
“The fix for a bug that I reported ended up introducing a function responsible for the hack,” wrote Kankodu in a post on X (formerly Twitter) yesterday.
On Euler, users can lend assets and receive liquidity provider tokens, known as eTokens, in return. These eTokens, such as eDAI for DAI deposits, represent the underlying asset deposited plus any interest earned. The amount of eTokens given is determined by an exchange rate that factors in the interest on the deposited asset.
Kankodu said that in July 2022, they reported the Euler “first deposit bug,” which is a separate issue from the March incident. This bug, which Kankudo found, could have allowed attackers to exploit Euler by artificially inflating exchange rates, enabling them to withdraw all tokens. They added that the Euler team awarded them $50,000 for the discovery.
Kankodu is a crypto whitehat, a term for an ethical hacker, ranking 17th at web3 bug bounty platform Immunefi, having submitted 28 paid reports with total earnings of $689,000.
The fix and its unintended consequence
To address the specific vulnerability, Kankodu stated that Euler implemented a feature where all new eTokens began with a total supply and reserve of 1 million wei, the smallest unit of ether. This change rendered an initial attack economically unfeasible. According to Kankodu, the approach mirrored that of Uniswap version 2 and was effective for new eTokens.
For existing eTokens with reserves below 1 million wei, Euler added a function called “donateToReserves.” While the function was designed to bring reserves above the 1 million wei threshold, it inadvertently created a larger vulnerability. The $200 million attack was executed by exploiting this “donateToReserves” function in combination with Euler’s unique liquidation mechanism.
“The white hat submitted the bug referenced in the tweet through Immunefi. Euler had a $1m bounty on offer for critical bugs at the time, but a $50k bounty was paid for this particular finding given its lower severity. Once a fix was developed, it was discussed briefly with the white hat, shared with other people familiar with the protocol, audited by a prior Euler auditor, and implemented following a governance vote,” said Michael Bentley, CEO of Euler Labs.
However, Euler Labs did not comment on whether the earlier bug report directly led to the subsequent massive hack.
Euler’s $200 million hack and recovery
The March 13 flash-loan attack on Euler resulted in a loss of nearly $200 million across multiple assets. These included $136 million in staked ether (stETH), $34 million in USDC, $19 million in wrapped bitcoin (WBTC), and $8.7 million in DAI.
Flash loans, although useful in the DeFi sector for legitimate purposes, are often exploited by attackers due to the lack of required collateral. However, these loans come with high risk, as they must be repaid within a very short timeframe.
Following the attack, Euler’s EUL token experienced a nearly 70% decrease in value, falling to $2.07. As of the most recent data from CoinGecko, the token is now trading at $2.58.
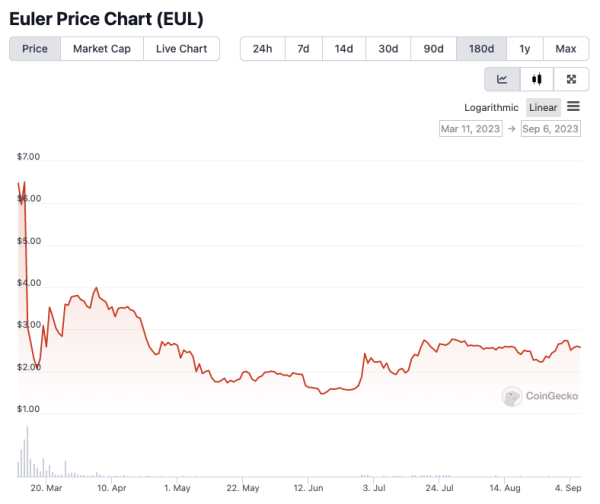
EUL/USD price chart. Image: CoinGecko.
The attacker later returned $177 million in a series of transactions in March and April, accounting for the expected “recoverable funds” from the hack after adjusting for a bounty offered by the project.
“Following successful negotiations, all of the recoverable funds taken from the Euler protocol on March 13 have now been successfully returned by the exploiter,” project developer Euler Labs said at the time.
With reporting assistance from Vishal Chawla.