NFT ‘sleepdrops’ have drained $11.5 million from Ethereum users
A research report by web3 security specialists Forta Network and Blockfence detailed how a scam operation targeting Ethereum users known as “sleepdropping” has resulted in losses totaling $11.5 million since it was first spotted in December 2022.
The scam operates by dispatching seemingly authentic ERC-1155 tokens, often NFTs, to unaware users. This tactic lures users to deceptive websites where they’re tricked into authorizing transactions, inadvertently funneling their assets into the scammer’s possession. The culprits behind the operation remain unidentified.
According to Forta Network and Blockfence, over half a million addresses have been recipients of these misleading token airdrops. Currently, more than 20,000 users have been confirmed to have fallen victim.
Counterfeit NFT airdrops used to steal funds
In one documented instance, users received a sham Lido NFT token, presenting itself as a “badge” to claim an airdrop.
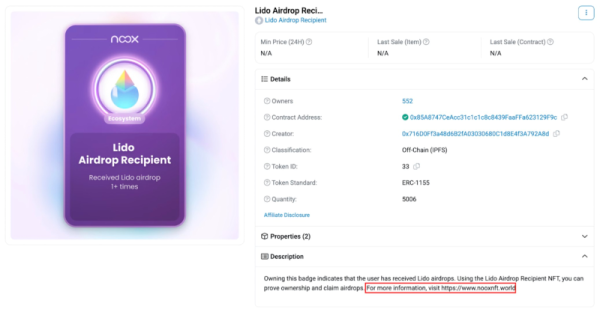
An example of an NFT “sleepdrop” scam. Source: Forta
On its own, the NFT doesn’t compromise a user’s wallet. However, if users perceive the airdrop as legitimate, their curiosity might lead them to interact with the token, possibly claiming malicious tokens on a deceptive site.
The distribution appeared to originate from an authentic smart contract that, back in 2021, had issued an airdrop to early Lido stakers. The intricate technical aspects of ERC token contracts allow it to be manipulated, even when genuine.
“A savvy user might review the transfer in more detail and see that the token is being transferred from the legitimate Lido: Early Stakers Airdrop account,” Forta said in the report. “This is a deception the scammer executes by taking advantage of the implementation of ERC token contracts.”
The research from Forta and Blockfence identified over 100 distinct smart contracts associated with the scam operation that exhibit similar deployment patterns. The research also outlined the scam’s three primary stages: the deceptive airdrop operations sending NFTs that appear to come from trustworthy sources, websites designed to mislead users, and the malicious contracts that ultimately trick users into transferring their funds.